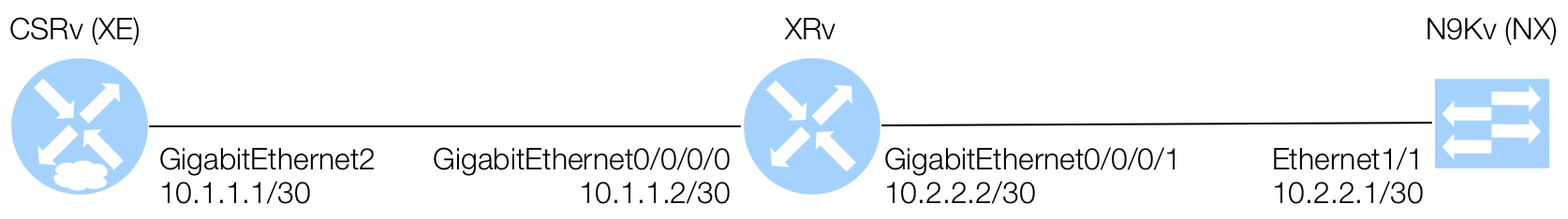
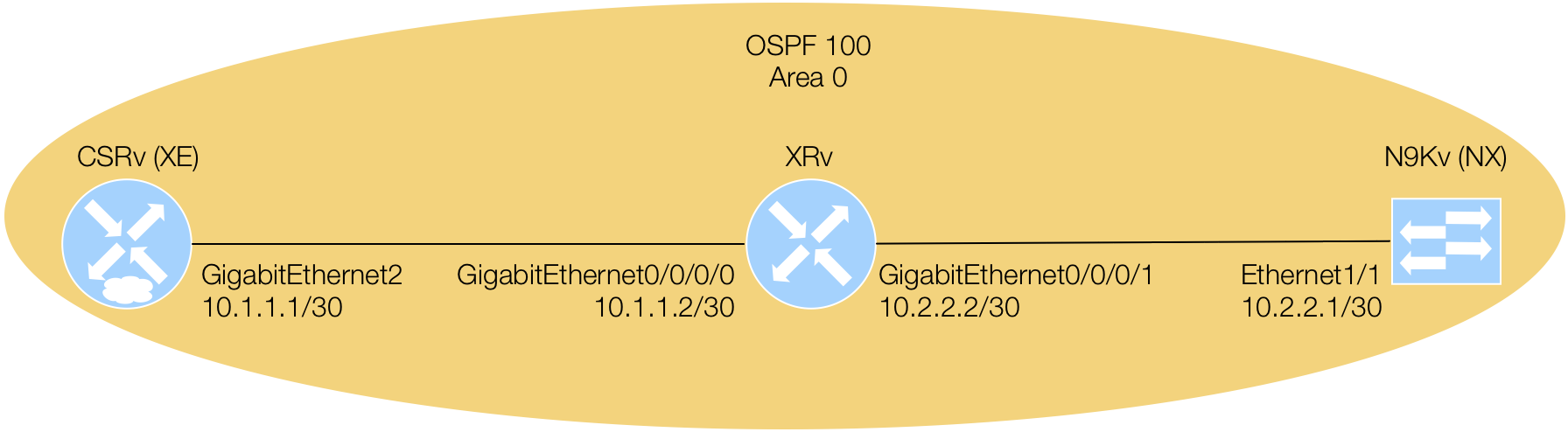
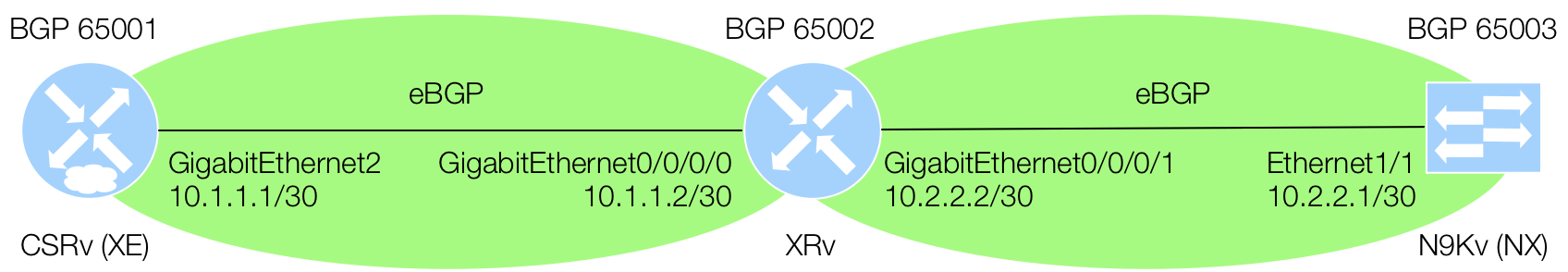
Get Capabilities via Terminal
Exchange NETCONF Capabilities
As mentioned in the Introduction to NETCONF, the client and server exchange a hello containing capabilities. In your Terminal window, within your Docker container, you can ssh to the NETCONF service to see these capabilities. It's important to understand the capabilities that exist on and between each platform for correlating to feature/functionality you may be using today. Again, the IETF and OpenConfig models have less features than the native platform models.
*Note: The output of capabilities is lengthy and synonymous with what is found on GitHub: https://github.com/YangModels/yang/tree/master/vendor/cisco
Remember, NETCONF operates per industry standard on port 830. When you perform this test operation on a
terminal window, i.e. command line (CLI), you must specify the port as to not use the default SSH port of 22.
This is achieved by using the -p SSH option.
Further, you can use another SSH option to invoke a subsystem on the server side. In this case, you want to
invoke the NETCONF subsystem on the server side, i.e. the network device. This is achieved by using the
-s SSH option. Upon successful connections, you could actually send and receive NETCONF RPCs this
way; HOWEVER, we will not being do that in this lab...there are better ways to NETCONF!
Below, you're going to connect via the CLI just to see the capabilities of each platform. NOTE, this is a lot of output for the CLI. The lab will later teach you how to get this same data programmatically!
Get XE NETCONF Capabilities
In your Docker container, SSH to your XE device's NETCONF service using the below ssh command and password cisco.123 to exchange capabilities:
ssh admin@10.2.100.11 -p 830 -s netconf
The return capabilities can be found below for your reference. If you executed the SSH command, be sure to
execute Ctrl+c to disconnect from the session.
<?xml version="1.0" encoding="UTF-8"?>
<hello xmlns="urn:ietf:params:xml:ns:netconf:base:1.0">
<capabilities>
<capability>urn:ietf:params:netconf:base:1.0</capability>
<capability>urn:ietf:params:netconf:base:1.1</capability>
<capability>urn:ietf:params:netconf:capability:writable-running:1.0</capability>
<capability>urn:ietf:params:netconf:capability:xpath:1.0</capability>
<capability>urn:ietf:params:netconf:capability:validate:1.0</capability>
<capability>urn:ietf:params:netconf:capability:validate:1.1</capability>
<capability>urn:ietf:params:netconf:capability:rollback-on-error:1.0</capability>
<capability>urn:ietf:params:netconf:capability:notification:1.0</capability>
<capability>urn:ietf:params:netconf:capability:interleave:1.0</capability>
<capability>urn:ietf:params:netconf:capability:with-defaults:1.0?basic-mode=explicit&also-supported=report-all-tagged</capability>
<capability>urn:ietf:params:netconf:capability:yang-library:1.0?revision=2016-06-21&module-set-id=51d8cd742edef02cb7066f31ef95001d</capability>
<capability>http://tail-f.com/ns/netconf/actions/1.0</capability>
<capability>http://tail-f.com/ns/netconf/extensions</capability>
<capability>http://cisco.com/ns/cisco-xe-ietf-ip-deviation?module=cisco-xe-ietf-ip-deviation&revision=2016-08-10</capability>
<capability>http://cisco.com/ns/cisco-xe-ietf-ipv4-unicast-routing-deviation?module=cisco-xe-ietf-ipv4-unicast-routing-deviation&revision=2015-09-11</capability>
<capability>http://cisco.com/ns/cisco-xe-ietf-ipv6-unicast-routing-deviation?module=cisco-xe-ietf-ipv6-unicast-routing-deviation&revision=2015-09-11</capability>
(... output truncated ...)
</capabilities>
<session-id>58</session-id></hello>]]>]]>
Be sure to
execute Ctrl+c to disconnect from the session.
Get XR NETCONF Capabilities
In your Docker container, SSH to your XR device's NETCONF service using the below ssh command and password cisco.123 to exchange capabilities:
ssh admin@10.2.100.12 -p 830 -s netconf
The return capabilities can be found below for your reference. If you executed the SSH command, be sure to
execute Ctrl+c to disconnect from the session.
<hello xmlns="urn:ietf:params:xml:ns:netconf:base:1.0">
<capabilities>
<capability>urn:ietf:params:netconf:base:1.1</capability>
<capability>urn:ietf:params:netconf:capability:candidate:1.0</capability>
<capability>urn:ietf:params:netconf:capability:rollback-on-error:1.0</capability>
<capability>urn:ietf:params:netconf:capability:validate:1.1</capability>
<capability>urn:ietf:params:netconf:capability:confirmed-commit:1.1</capability>
<capability>urn:ietf:params:xml:ns:yang:ietf-netconf-monitoring?module=ietf-netconf-monitoring&revision=2010-10-04&deviations=cisco-xr-ietf-netconf-monitoring-deviations</capability>
<capability>http://cisco.com/ns/yang/cisco-xr-ietf-netconf-monitoring-deviations?module=cisco-xr-ietf-netconf-monitoring-deviations&revision=2016-02-16</capability>
<capability>http://cisco.com/ns/yang/Cisco-IOS-XR-pbr-vservice-ea-oper?module=Cisco-IOS-XR-pbr-vservice-ea-oper&revision=2017-05-01</capability>
<capability>http://cisco.com/ns/yang/Cisco-IOS-XR-infra-rsi-oper?module=Cisco-IOS-XR-infra-rsi-oper&revision=2017-05-01</capability>
<capability>http://cisco.com/ns/yang/cisco-xr-types?module=Cisco-IOS-XR-types&revision=2017-03-07</capability>
<capability>http://cisco.com/ns/yang/Cisco-IOS-XR-flashmib-cfg?module=Cisco-IOS-XR-flashmib-cfg&revision=2015-12-15</capability>
(... output truncated ...)
<capability>http://cisco.com/panini/calvados/fit?module=fit&revision=2012-05-20</capability>
<capability>http://www.cisco.com/ns/yang/Cisco-IOS-XR-sysadmin-rvm-mgr?module=Cisco-IOS-XR-sysadmin-rvm-mgr&revision=2017-04-12</capability>
</capabilities>
<session-id>2212180000</session-id>
</hello>
]]>]]>
Be sure to
execute Ctrl+c to disconnect from the session.
Get NX NETCONF Capabilities
In your Docker container, SSH to your NX device's NETCONF service using the below ssh command and password cisco.123 to exchange capabilities:
ssh admin@10.2.100.13 -p 830 -s netconf
The return capabilities can be found below for your reference. If you executed the SSH command, be sure to
execute Ctrl+c to disconnect from the session.
<?xml version="1.0" encoding="UTF-8"?>
<hello xmlns="urn:ietf:params:xml:ns:netconf:base:1.0">
<capabilities>
<capability>urn:ietf:params:netconf:base:1.0</capability>
<capability>urn:ietf:params:netconf:base:1.1</capability>
<capability>urn:ietf:params:netconf:capability:writable-running:1.0</capability>
<capability>urn:ietf:params:netconf:capability:rollback-on-error:1.0</capability>
<capability>urn:ietf:params:netconf:capability:candidate:1.0</capability>
<capability>urn:ietf:params:netconf:capability:validate:1.1</capability>
<capability>urn:ietf:params:netconf:capability:confirmed-commit:1.1</capability>
<capability>http://cisco.com/ns/yang/cisco-nx-os-device?revision=2018-02-12&module=Cisco-NX-OS-device&deviations=Cisco-NX-OS-device-deviations</capability>
<capability>http://openconfig.net/yang/bgp?revision=2016-06-06&module=openconfig-bgp&deviations=openconfig-bgp-deviations</capability>
<capability>http://openconfig.net/yang/bgp-multiprotocol?revision=2016-06-06&module=openconfig-bgp-multiprotocol&deviations=openconfig-bgp-multiprotocol-deviations</capability>
<capability>http://openconfig.net/yang/interfaces?revision=2016-05-26&module=openconfig-interfaces&deviations=openconfig-interfaces-deviations</capability>
<capability>http://openconfig.net/yang/interfaces/ip?revision=2016-05-26&module=openconfig-if-ip&deviations=openconfig-if-ip-deviations</capability>
<capability>http://openconfig.net/yang/local-routing?revision=2016-05-11&module=openconfig-local-routing&deviations=openconfig-local-routing-deviations</capability>
<capability>http://openconfig.net/yang/routing-policy?revision=2016-05-12&module=openconfig-routing-policy&deviations=openconfig-routing-policy-deviations</capability>
<capability>http://openconfig.net/yang/vlan?revision=2016-05-26&module=openconfig-vlan&deviations=openconfig-vlan-deviations</capability>
</capabilities>
<session-id>681081650</session-id>
</hello>
]]>]]>
Be sure to
execute Ctrl+c to disconnect from the session.
DO NOT NETCONF LIKE THIS!
In each of these exchanges, you could actually sit here and exchange RPCs, but do not NETCONF in this fashion. There are better ways to interact with the NETCONF enabled device such as Ansible using a NETCONF plugin or in Python directly. Lets look at these options in the next few sections of the lab.