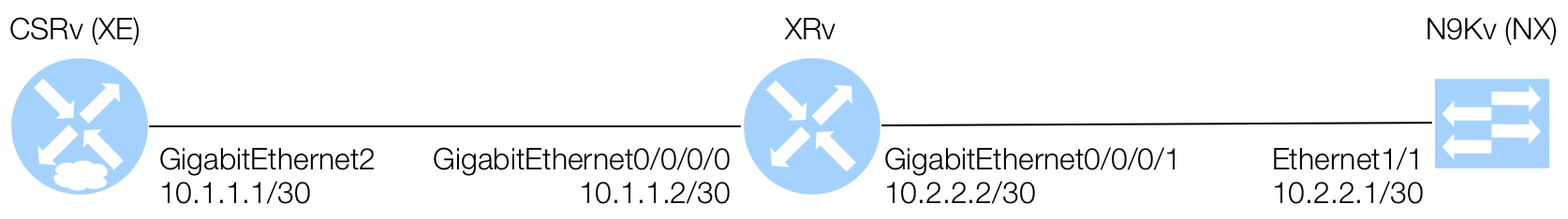
Verify MDP Interfaces are Enabled
In this section of the lab, you are simply going to perform verification steps to confirm that the NETCONF and/or RESTCONF API interfaces have been enabled.
In your Terminal window, within your Docker container, there are preconfigured CLI aliases. Simply issuing
xe, xr, or nx will connect you to your pod devices via SSH. All
passwords are cisco.123.
Note: The first time you connect to the xe, xr, or nx devices in this lab, you will be presented with this message:
The authenticity of host '10.2.103.11 (10.2.103.11)' can't be established.
RSA key fingerprint is SHA256:v8bxjY1jWsEv0jTnyG0JfIzfhzp2ZmV59ekY4rwIcJc.
RSA key fingerprint is MD5:14:bf:2f:14:1b:ab:b6:6d:37:05:e9:c3:2f:22:5a:50.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '10.2.103.11' (RSA) to the list of known hosts.
Type yes and hit enter when prompted.
Connect to XE Device
Connect to your XE device within your Docker container and verify the configuration:
xe
Use a password of cisco.123.
Check that NETCONF has been enabled by issuing show run | inc netconf:
show run | inc netconf
The output should look similar to the below:
Pod00-CSRv#show run | inc netconf
netconf-yang
Pod00-CSRv#
Check that RESTCONF has been enabled by issuing show run | inc restconf:
show run | inc restconf
The output should look similar to the below:
Pod00-CSRv#show run | inc restconf
restconf
Pod00-CSRv#
Check that NETCONF Datastore that is used by the XE platform by issuing
show netconf-yang datastores:
show netconf-yang datastores
The output should look similar to the below:
Pod00-CSRv#show netconf-yang datastores
Datastore Name : running
Pod00-CSRv#
The XE platform allows you to check your NETCONF statistics in the context of RPCs and associated sessions.
This can be useful for tracking or troubleshooting. This command is show netconf-yang statistics.
show netconf-yang statistics
The output for you XE device should similar to the below. Do not worry if it does not show any increases in the stats fields at this point in time.
Pod00-CSRv#show netconf-yang statistics
netconf-start-time : 2018-04-24T00:26:52+00:00
in-rpcs : 0
in-bad-rpcs : 0
out-rpc-errors : 0
out-notifications : 0
in-sessions : 0
dropped-sessions : 0
in-bad-hellos : 0
Pod00-CSRv#
We'll now proceed to checking your XR device. Type exit or copy the exit below to quit your SSH session to the XE device and return back to your container prompt.
exit
Connect to XR Device
Connect to your XR device within your Docker container and verify the configuration:
xr
Use a password of cisco.123.
Check that NETCONF has been enabled by issuing show run | inc netconf:
show run | inc netconf
The output should look similar to the below:
RP/0/RP0/CPU0:Pod00-XRv9K-XR#show run | inc netconf
Tue Apr 24 09:37:16.899 UTC
Building configuration...
netconf-yang agent
ssh server netconf vrf management
RP/0/RP0/CPU0:Pod00-XRv#
Like the XE platform, the XR platform can display NETCONF statistics, but in a much more granular fashion. The
command to for this is the same as for the XE platform; show netconf-yang statistics.
show netconf-yang statistics
Again, do not worry if your output at this point in time does not match exactly below. As you can see, the fields are not just classified as RPCs and sessions, but rather, the type of RPC. This is very useful for troubleshooting and understanding exactly which types of RPCs may be having issues.
RP/0/RP0/CPU0:Pod00-XRv#show netconf-yang statistics
Tue Apr 24 09:37:08.229 UTC
Summary statistics
# requests| total time| min time per request| max time per request| avg time per request|
other 0| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms|
close-session 0| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms|
kill-session 0| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms|
get-schema 0| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms|
get 0| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms|
get-config 0| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms|
edit-config 0| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms|
commit 0| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms|
cancel-commit 0| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms|
lock 0| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms|
unlock 0| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms|
discard-changes 0| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms|
validate 0| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms|
xml parse 0| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms|
netconf processor 0| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms|
YFW 0| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms|
pending requests 0| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms|
invoke rpc 0| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms|
copy-config 0| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms|
create-subscription 0| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms| 0h 0m 0s 0ms|
RP/0/RP0/CPU0:Pod00-XRv#
We'll now proceed to checking your NX device. Type exit or copy the exit below to quit your SSH session to the XR device and return back to your container prompt.
exit
Connect to NX Device
Connect to your NX device within your Docker container and verify the configuration:
nx
Use a password of cisco.123.
Check that NETCONF and RESTCONF have been enabled by issuing show run | grep feature:
show run | grep feature
The output should look similar to the below:
Pod00-N9Kv# show run | grep feature
feature nxapi
feature bash-shell
feature scp-server
feature netconf
feature restconf
Pod00-N9Kv#
At this point in time, the NX platform doesn't have many more show commands implemented to show statistics. When
done, exit your NX device by typing or copying the exit below.
exit
XR - Enable Netconf on Port 830
The XRv version we are using for this lab has a nuance such that one must set the netconf port to 22, commit, and then back to 830 and commit a second time. We've taken care of this for you with the following set of steps.
Install Netmiko
We need the Python package netmiko for this next step.
In your container, execute the following:
pip3.6 install netmiko
Create The Script
Create a new script in your workspace named the following:
netmiko_xr_port.py
Populate the script with the following Python:
# Imports required
from netmiko import ConnectHandler
duts = {"xrv": '10.2.100.12'}
device = {'device_type': 'cisco_xr', 'ip': duts['xrv'], 'username': 'admin', 'password': 'cisco.123'}
netmiko_connection = ConnectHandler(**device)
netmiko_connection.find_prompt()
commands = ["ssh server netconf port 22"]
netmiko_connection.send_config_set(commands)
commands = ["ssh server netconf port 830"]
netmiko_connection.send_config_set(commands)
netmiko_connection.disconnect()
print("Done applying XR config!")
Execute XR SSH Server Port Fixup Script
Execute this script in your container as follows:
python3.6 netmiko_xr_port.py
Observe the following output:
[root@73dfdfffbd8c workspace]# python3.6 netmiko_xr_port.py
Done applying XR config!
This uses Netmiko to apply the configuration over CLI. The script takes about 15 seconds to execute. We try to avoid CLI interaction where at all possible, but for some configuration we must fall back to it.
Wrapping Up
All of our MDP management interfaces are now enabled, let's move on to querying them!